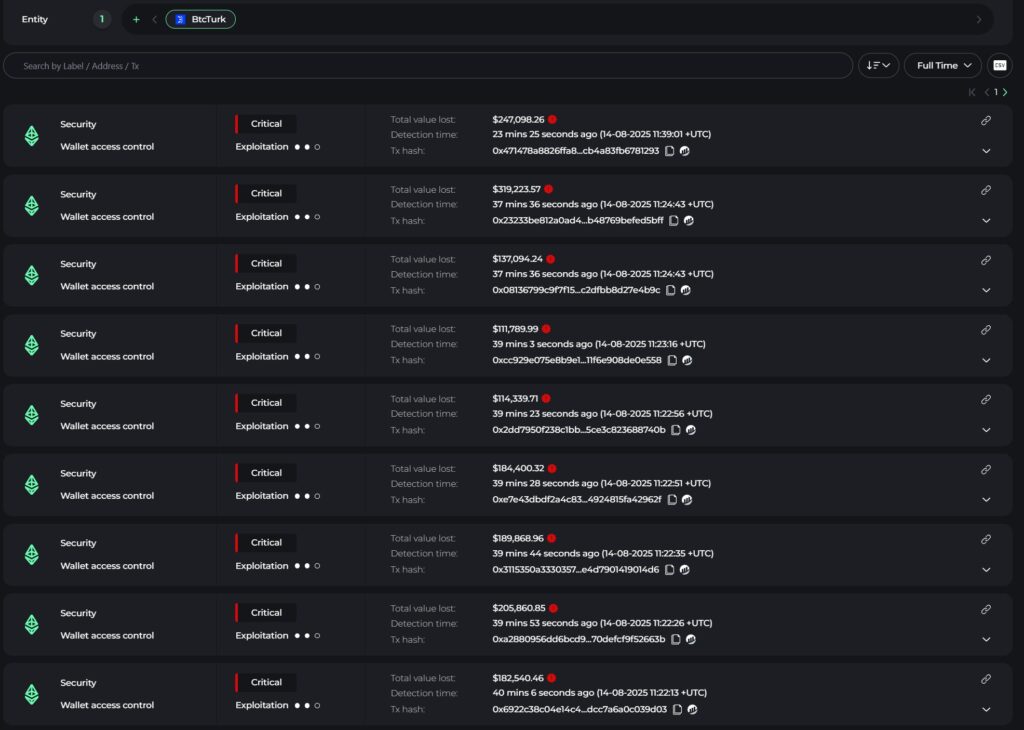
BtcTurk’s $48M Hack Deepens Crypto’s Summer of Security Failures
BtcTurk, Turkey’s second-largest cryptocurrency exchange, has become the latest casualty in a brutal summer for digital asset platforms. The exchange suffered a multi-chain hot wallet breach on August 14, resulting...

Vulnerability Assessment vs. Penetration Testing: Understanding the Difference and Why You Need Both
In today’s cybersecurity landscape, organizations face an ever-evolving threat environment. Cybercriminals are more sophisticated than ever, and security teams must stay one step ahead to protect critical systems and data....
Responsible Disclosure: What It Is, Why It Matters, and How to Do It Right
In today’s hyper-connected world, security vulnerabilities are inevitable — no matter how strong your defenses are. What truly defines an organization’s security posture isn’t the absence of vulnerabilities, but how...